
When a packet reaches our network, the first thing we see is where the IP address packet originates from. And we make decisions based on that IP address.
In this post, I will explain what these decisions are and if they make sense. Can we actually use an IP address as a decision point or not?
Ancient history
The Internet as we know it started on 1 January 1983 when ARPANET changed from NCP to the TCP/IP protocol suite. It went through a rapid evolution during the 1980s: In 1985, with the creation of the supercomputer centres program, NSF created NSFNET, a network that connected five supercomputer centres and provided a network for research and education. Then, based on the ARPANET protocols, the NSFNET created a national backbone service.
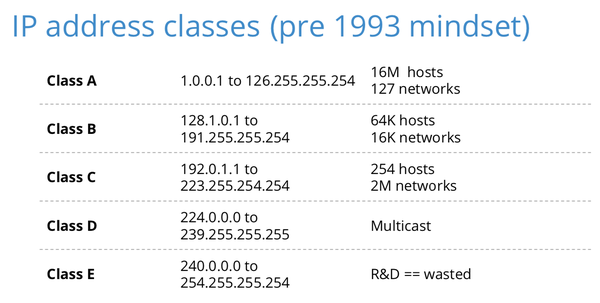
In 1987, the first Internet Service Providers (ISPs) were created. At that point in time, you would send a mail to IANA, or more precisely to Jon Postel, and ask for a block of IP addresses for your network. Usually, Jon would assign as many addresses to you as you had asked for — or more likely a bit more, because the address architecture looked like this:
Figure 1 — Classful IP address architecture.
Addresses were assigned on 8-bit boundaries. So, we ended up with a few very large blocks (class A), some mid-sized blocks (class B) and many small blocks (class C).
In addition to that, there was a range of addresses (class E) that were pretty much unusable because it was reserved for research and development and many operators today filter packets sent from those addresses.
When I got on the Internet some years ago, we could easily say that an IP address is a host. In those days, every computer on the Internet had a public IP address and a local host address (127.0.0.1.). So, we could say that an:
IP address = identity
However, it didn’t equal the identity of a user, but the identity of a host on the network. In those days, computers were expensive and one host could have had many hundreds of users.
In the late 1980s, the Internet started to grow exponentially and around 1990, we realized the classful addressing architecture described above was wrong and wouldn’t scale. The assigned blocks were either too big or too small, which overall, resulted in very low utilization.
Figure 2 — A map of the IPv4 address space according to xkcd.
So a new technology was developed, called Classless Interdomain Routing (CIDR) that allowed routing announcements not only on 8-bit boundaries but on all bit boundaries from a /8 to a /24.
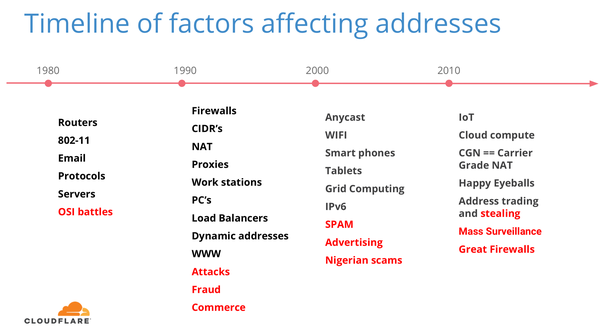
Over the years, all kinds of factors came into play that affected how we use and understand IP addresses — some made more sense than others (see Figure 3).
Figure 3 — Timeline of factors affecting IP addresses.
Where does this leave us?
Because of this rapid growth of the Internet, we have a diverse understanding of what an IP address is, which is largely based on your experience or even what you learned in school or university. For instance, Cloudflare operates an anycast-only network. That means all of our addresses are advertised in all of our locations. However, it turns out that a lot of people who are doing research in the field of network measurements do not take anycast into account, which basically means they do not understand how large parts of the Internet are operated today. This is scary.
So what do we actually want and need to know about IP addresses? The answer to that question very much depends on your perspective and viewpoint.
In essence, an IP address is just an identifier that helps the routing system to send packets around. But all kinds of other attributes can be attached to an IP address, including:
- The postal address of a registrant
- The location of a user
- Routing aspects: unicast vs anycast
- Services: email, DNS, HTTP, none
- History
- Abuse
Let’s look at some of these attributes in more detail.
Location, location, location
Location is a big thing today and many service providers base decisions on the location of the user, or what they think the location of the user is. Sometimes that is a good thing, so you can reach the content you are looking for faster. But sometimes providers do the wrong thing and the user ends up with ‘craptimization’ instead of ‘optimization’.
In addition to those annoyances, there are also things like privacy rules, GDPR, and an economy’s sovereignty. Different economies apply different rules and regulations and content that is legal in some economies might be illegal in others.
In Cloudflare’s case, we are also trying to optimize traffic based on location and answer the following questions:
- At which Point of Presence (PoP) does the IP address land?
- Where will it move to if the preferred PoP is ‘down’?
- What if the top two/three/four are down?
- What if the ‘transit’ provider goes down? Where will the alternative one take the IP address to?
Address reputation
Some people have decided that some IP addresses are good, and others are bad. How they make those decisions very much depends on what they consider bad. For instance, if an address sends spam, it means it is bad for mail providers, but does that mean it is also bad for a DNS provider?
There are all kinds of lists showing the quality or reputation of an address. But how accurate and up-to-date are those lists? Maybe an address that has been bad yesterday is not bad today?
In addition to all that, there is a whole industry that is trying to figure out who the user is behind an IP address. But didn’t we say above that an address identifies a device? Is that still the case? We invented Network Address Translation (NAT) and carrier-grade NAT and mobility. Do you know how many IP addresses your smartphone had in the last couple of days? Probably more than you think.
So, how long does an IP address live on your device? Some users get a static address if they pay extra. Others get dynamic address assignments, for a number of hours or days. Some people share addresses, other addresses are used for roaming.
Who ‘owns’ IP addresses?
Some of you might think you own the IP addresses you got from your Regional Internet Registry or your ISP. But just like with domain names, you actually lease them.
However, since there is a shortage of IPv4 addresses, they have become valuable and a transfer market has developed that is very lucrative for some and that has led to some abuse.
Note, you should not lend addresses to others. First of all, you don’t actually own them. And secondly, you never know what others will use these addresses for. It is very hard to restore a good reputation.
Think about an IP address as a temporary identifier
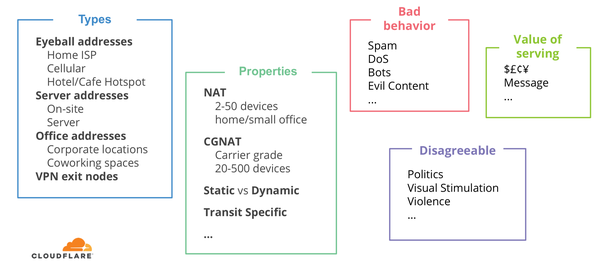
Different types of services attach different values to an IP address. See Figure 4 for an overview of the types of values that can be attached to the same IP address, based on the service you’re providing.
Figure 4 — Types of values that can be attached to the same IP address.
Think about an IP address as a temporary identifier. Also, the value you attach to an address very much depends on the type of business you are in. If you are in the filtering business, think about an IP address as an identifier with temporary accuracy. It can change.
Let’s keep the Internet open and trustworthy!
This was presented at the RIPE 78 meeting in Reykjavik.
Adapted from original post which appeared first on RIPE Labs.
Ólafur Guðmundsson is an Engineering Director at Cloudflare and an active participant in the IETF.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

Hi, Ólafur :
0) Thank you for your tutorial on IPv4 history and consequences. It is very informative.
1) A few keywords in your article caught my eyes. For example:
A. “Class E … R&D == wasted”
B. “IP address = identity ”
C. “Location, location, location ”
D. “geolocation”
E. etc.
These are parts of the intertwined, and sometimes convoluted Internet topics having no consistent resolution, so far.
2) I would like to draw your attention to a draft IETF proposal that is the result of our study efforts:
https://tools.ietf.org/html/draft-chen-ati-adaptive-ipv4-address-space-05
I look forward to your thoughts,
Abe (2019-07-22 08:05)
Abe,
on #2 just use IPv6
Hi, Ólafur :
0) With your in-depth knowledge of IPv4’s history and understanding of its properties, I was hoping to learn something more specific about where the Internet should be heading. Instead, I am surprised at the quick and brief recommendation that seems to be based on the common perception of the IPv6.
1) The four Topics that I itemized are known issues with the IPv4. However, are we sure that the IPv6 has adequately addressed these and will not step into them again, for sure? Allow me to expand my comment a bit in the context of our work, named EzIP (Phonetic for Easy IPv4) Project.
2) Topic A.: This is the most puzzling fact that persuaded us to pursue the EzIP Project. That is, how could we leave 1/16th of the entire IPv4 address pool “RESERVED for Future use” while putting an end to IPv4’s life by declaring that its address pool has been depleted? Is there any justification anywhere? Precisely as you identified, we could not just stand on the sideline letting it really going into the waste. EzIP makes use of the Class E block to expand the IPv4 address by 256M (Million) folds, resulted in a resource that is 20M times of the IoT demand, 50B (Billion) by 2020, as projected by Cisco. So that, the primary reason to move onto IPv6 is removed.
3) Topics B. – D.: These are all related to the curious differences between the deterministic characteristics of the PSTN and those of the Internet. From the communications principle point of view, the latter are quite an unnecessary complication, if at all avoidable. EzIP resolved this issue by modifying the Internet operation in a new extension called RAN (Regional Area Network) which follows the old teaching.
4) Topic E.: As implied, cyber security vulnerability is induced by Pt. 3) above. With Pt. 2) properly resolved, issues in Pt. 3) can be consequentially dealt with. EzIP will mitigate the root cause of this overall concern significantly.
5) I would appreciate very much if you could comment on the above trend of thoughts, after you had a chance to review at least the Abstract and the Appendix C. of the cited IETF Draft paper.
Thanks a lot,
Abe (2019-07-26 09:44)
I didn’t realize that IPV4 addresses were created back in 1983. It surprises me that we haven’t completely switched over to IPV6 addresses. Would technology have to change quite a bit in order for that to happen?
Hi, Shaylee:
In the old days, engineers were trained to review a project from the angle of “If it isn’t broken, do not touch it”. There were other more important things for us to make use of our resources. We did not create a new “technology / approach” just for the sake of having fun with it.
I was very puzzled by the whole IPv6 initiative, until I found out that one sixteenth of the existing IPv4 address was even not being used (Reserved for Future Use)! why would anyone go into a boxing ring with one arm tied to the back?
From there, I discovered that there is a way to make use of it to resolve the IPv4 shortage issue, simply by mimicking the PSTN.
Furthermore, Cyber security vulnerability can be mitigated with deterministic administration, because IP Address == Identification can be established again on individual basis, just like the good old telephone number.
It is kind of “Back to the Future”.
Hope these helps.
Abe (2020-06-02 11:33 EDT)
Good