
Since 1997, the Malaysia Computer Emergency Response Team (MyCERT) has played a leading role as the national technical reference centre in responding to and advising on cybersecurity incidents in Malaysia, working closely with law enforcement agencies such as the Royal Malaysian Police and Securities Commission, as well as ISPs and other CERTs nationally and worldwide.
However, in the past three years there has been a significant increase in requests for support from end users, which mirrors the huge upswing of cybercrime targeting the general public. In September this year, Malaysian Police reported that around 1,300 Malaysians had lost more than RM83 million to ‘love scams’ so far this year.
Such fraudulent ‘phishing’ scams—that aim to gather personal information using deceptive emails and websites—along with intrusions and malicious codes, have been among the most common cybersecurity incidents reported to MyCERT in the past three years.
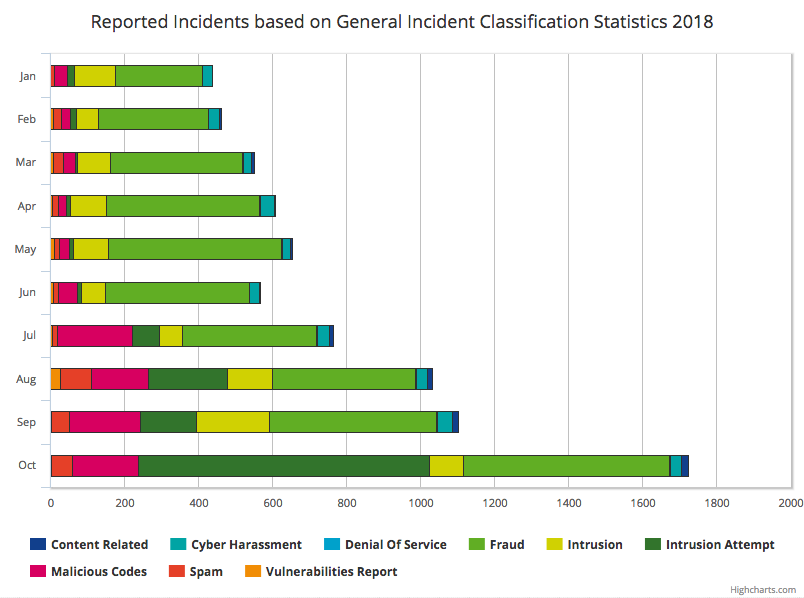 Figure 1 — Reported incidents based on General Incident Classification statistics as of October 2018 | MyCERT Stats
Figure 1 — Reported incidents based on General Incident Classification statistics as of October 2018 | MyCERT Stats
“Most phishing attacks in Malaysia target bank customers and users of social media sites,” says Megat Muazzam Abdul Mutalib, Head of MyCERT.
Given that the human factor is an evergreen problem in cybersecurity, “these are often the same infiltration points attackers use against large corporations as well”.
Apart from issuing alerts and advisories about such scams, MyCERT was also involved in a public awareness and outreach program known as Cyber Security Awareness for Everyone (CyberSAFE), which has educated more than 230,000 school students and corporate staff on how to protect themselves from online threats.
“The best form of incident response is mitigating the threat in the first place,” says Sharifah Roziah Mohd Kassim who manages MyCERT’s Security Operation Centre. “CyberSAFE provides information and resources to targeted groups for them to be able to make informed choices and manage the cybersecurity issues.”
MyCERT has also developed an anti-phishing add-on for Google Chrome and Mozilla Firefox, DontPhishMe, which uses pattern matching techniques to enable Malaysian Internet users to protect themselves against online banking phishing websites.
This need to support end-users isn’t limited to Malaysia, rather it reflects the growing role that CERTs are playing in their economies; many established CERTs are identifying and acting upon key areas that add value to the overall security efforts that law enforcement agencies, ISPs and software developers are implementing.
Cyber Threat Intelligence improving incident response
Information and data are among the most valuable assets of any organization. Their exact worth depends though on how good (correct and reliable) they are as well as how well an organization is equipped to analyse them.
This is one of the reasons why MyCERT has sought to make Cyber Threat Intelligence (CTI) an increasingly more important component of its incident response services over the last five years.
“CTI is another proactive mechanism we have implemented to both collect intelligence and identify possible cyber threats in a faster and more effective manner,” explains Sharifah Roziah.
“We are collecting open source intelligence, CTI data from our partners and CERTs and using common analysis tools, including Malware Information Sharing Platform (MISP), for detecting, analysing, and sharing the threat intelligence information we find with our partners, locally and internationally.”
Check out MyCERT’s Incidents Statistics and Advisory Reports
“To assist in this process we are broadening our collaboration with local entities, including the financial, government and private sectors to share threat intelligence information they are collecting with MyCERT and taking greater responsibility for their network security as well as for the Malaysia constituency.”
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.
