The Internet of Things (IoT) emerged as a complex cyber-physical system that allows smart devices to sense the environment and modify it accordingly to enhance the way we work and live. The existence of such a large network of interconnected entities poses major security and privacy issues that prevent its wide adoption.
This article discusses how to establish operating-system-level support for a wireless sensor network that requires run-time security in a way that doesn’t impair the performance and behaviour of the network.
Smart sensing brings a value
Adding intelligence to diverse application domains such as military and crime prevention, environment, industry and agriculture, urbanization, and infrastructure brings the advantages of more efficient operation and swift reactions to necessary changes. This has proved to provide both economic and sustainability benefits, as resources like energy and water are not wasted, and product quality and customer satisfaction remain high.
Wireless Sensor Networks (WSNs) are considered one of the core technologies in implementing IoT architectures. WSNs are systems of low-cost, low-power, resource constrained devices with sensors and radio transceivers used for communication. Their intelligence and power depend on the sum of their parts, their network and interaction, and the costs of operating dependably, safely, securely, efficiently and in real-time.
Communication protocols lack security
WSN architectures use a range of communication protocols to satisfy the communication needs of diverse applications. The most popular ones are the standards developed by the IETF that can be layered on top of each other. These are: IEEE 802.15.4(e), 6LoWPAN, RPL and CoAP.
Additionally, our study considers MAC layer protocols such as B-MAC and two collection routing protocols: the Backpressure Collection Protocol (BCP) and the Collection Tree Protocol (CTP). B-MAC is one of the few specialized MAC protocols. Its implementation was tested in hardware and it was used as a basis for the development of many other low-power MAC protocols. BCP makes routing and forwarding decisions on a per-packet basis without routes establishment, while CTP is a tree-based protocol closely related to RPL.
Even though these protocols use the limited capabilities of sensor nodes, the majority of them have not been designed with a security goal in mind. The diverse application range of WSNs mean that they are often deployed in publicly accessible environments, and are vulnerable to attacks that can disrupt their network communication. The attacks can be simple radio-level attacks such as radio jamming, or more challenging network-level attacks where one or more sensor nodes are compromised such that they behave in a malicious manner.
An attack leads to data loss
We address the attacks specific to the network layer. A malicious node (i.e. an attacker) can be enabled
- to spoof, alter or replay information, which can be considered the most direct attack on a routing protocol
- to selectively forward information or, in the worst-case scenario, fail to forward any data packets (blackhole attack)
- to flood the network by broadcasting a hello packet to the whole network
- to lure the traffic from a particular area by advertising false information to other nodes (sinkhole attack)
- or to present multiple identities in the network which would potentially create false routes for transmission (sybil attack).
The aim of these attacks is to delay, reduce or stop the flow of sensor data to the base station. This will compromise system functionality and cause failure or worse. In critical application systems, this could lead to a large economic loss with potential impact on the welfare of citizens.
Cooja tool to measure the disruption
Understanding the impact and behaviour will be necessary when protecting the network. By extending the features of Cooja (Contiki OS network simulator) we were able to measure and quantify disruptions caused by an attack.
In the simulation scenarios, we explored the impact of most common network-layer attacks to the network performance for RPL-based network. The first scenario is free from any malicious activity and is used as a benchmark for evaluating the effects of the attacks. The second scenario replicates the malicious activity, where a malicious node can perform one of the network layer attacks. Additionally, we consider the effect of having more than one malicious node in the network.
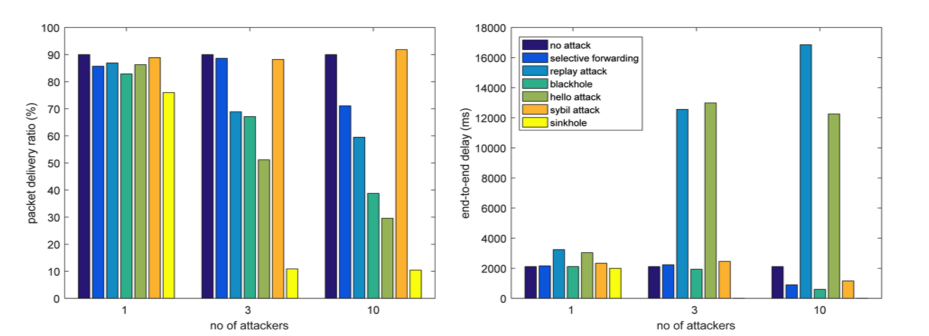
To gain an insight concerning the performance of RPL in the presence of a malicious node, we use the Packet Delivery Ratio PDR (the ratio between the total number of packets successfully received by the sink and the number of packets sent by the nodes) and End-to-End (E2E) delay (the average time needed for a packet to travel between the source and the destination). The results are depicted in Figure 1.
Figure 1: PDR and E2E delay of the network in the presence of a malicious node/malicious nodes performing different network-layer attacks
The attacks can be grouped into three categories, as follows:
- Attacks that reduce both, PDR and E2E delay, as the malicious nodes drop data that allows faster delivery of unaffected packets in the network (selective forwarding, blackhole, sinkhole)
- Attacks that reduce PDR, but increase E2E delay due to an increase in the total number of packets in the network (replay attack, hello flood attack) and
- Attacks that do not affect any of the metrics drastically (sybil attack) as some additional metrics might be needed.
If we want to implement a new countermeasure, we can easily identify its energy overhead, as well as its resilience towards built-in attacks. This will allow us to test the countermeasure before actual deployment. Therefore, it would be of great interest to the research community to have access to a security module within the Cooja, such as one developed in our work, which replicates the most common and most destructive attacks on the WSNs. This could serve as a benchmark to develop and test new security mechanisms which would contribute to faster developments in this research area.
A novel self-healing scheme to defend the network
We propose a lightweight, fully-distributed solution to enable WSNs to detect and recover from common attack scenarios.
Each sensor node builds a trust model of its neighbourhood using network overhearing, which it uses to autonomously adapt routing decisions. This allows data to flow around regions of the network affected by an attack. Mobile agents further bound the damage caused by attacks by using a simple notification scheme which propagates routing decisions from the affected areas to the sink.
An implementation of the Contiki operating system demonstrates the effectiveness and efficiency of the system. Our scheme is agnostic to WSN operating systems and routing layers and achieves low overheads of 1% on average and a detection reliability of 99.3% tested across various network sizes, attack scenarios and intensities.
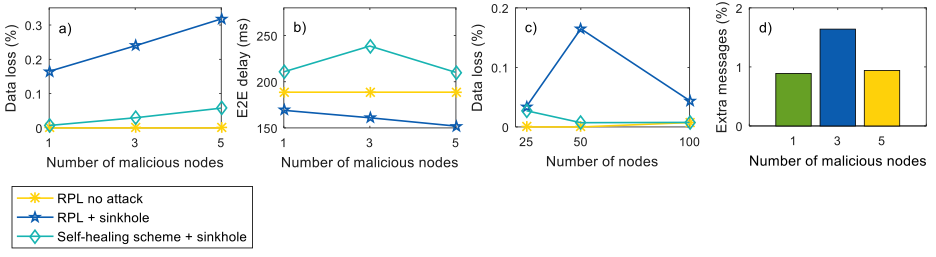
The results for the case of sinkhole attack are depicted in Figure 2.
Figure 2: Self-healing scheme performance for sinkhole attack: a) Data loss (%) in 50 nodes network with different intensities of the attack (1, 3 and 5 sinkhole nodes) b) E2E delay (ms) in 50 nodes network with different intensities of the attack (1, 3 and 5 sinkhole nodes) c) Data loss (%) in 25, 50 and 100 nodes networks with a single attacker d) Overhead of the self-healing scheme (% of extra messages) in 50 nodes network with different intensities of the attack (1, 3 and 5 sinkhole nodes).
The results show that our solution reduces the data loss rate caused by sinkhole attacks down to 1% (2.4% on average). Some additional transmission delay is incurred. This is due to the longer routes created to avoid the affected area. The overheads are very low: 1.16% extra messages on average. More detailed results for a larger number of attacks will be available soon via publication.
More information and next steps
This work was presented at the SEE 6 meeting in June 2017. Please refer to the video and the slides for more info. The research goals presented here will be further explored within two projects: Cisco/Silicon Valley Community Foundation — Fog to the FIELD and S4 (EPSRC Programme Grant): Science for Sensor Systems Software.
We welcome feedback on the results presented as we embark on the next steps.
Original post appeared on RIPE Labs. Contributor: Professor Julie A. McCann
Dr Ivana Tomic is currently working as a Research Associate in the AESE group at Imperial College London.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

The Wireless Temperature Sensor fascinates me. This article has significantly enhanced my comprehension of this technology. Now I will undoubtedly apply this technology to the advancement of my company(UbiBot). It’s a fantastic topic. It is currently one of the world’s most advanced technologies. Thank you for bringing up such a fascinating topic.