During 2014, smishing—or SMSphising— accounted for 380 million Korean Won (KRW) (over 336K USD) in fraud among Korean mobile phone users.
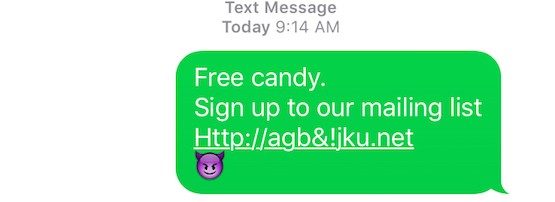
Smishing is a form of cybersecurity attack in which attackers include phishing URLs in the body of SMS text messages in order to hack into people’s smartphones to make purchases or steal personal information. It is a growing form of cybercrime in South Korea and one that is evolving.
How did it start?
Smishing first became prevalent with the introduction of micropayments via smartphones.
Micropayments are a convenient payment service where small, every-day payments, up to a maximum of 300K KRW a month, can be made using your smartphone and charged to your monthly phone bill. I often use micropayment to give a small present such as cake, ice cream or coffee coupon to my friends or nieces.
Micropayment requests only require a simple user authentication – a pin code transferred via SMS. The simplicity of this allowed criminals to strike.
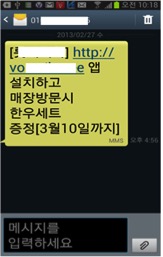
I first accounted smishing two years ago, when I was sent a free coupon from a popular burger franchise here in Korea. This is a popular scam where attackers send a fake promotion message with a malicious application download URL in the message body to people randomly. An example of the SMS message might be:
XX Berger | install the application | get a free burger
It looks like a free promotion coupon from a reliable franchise with its logo, so people download and install the malicious application without questioning it.
Once the malware has been downloaded, attackers can ‘sniff’ SMS messages for authentication codes. Attackers even can pay with the infected users phone’s micropayment system.
Victims will only notice fraudulent charges on their monthly bill. Some may not for many months if payments aren’t large or out of the ordinary.
How did it evolve?
As smishing became more prevalent, more and more people became wary of free coupons. Mobile networks and the Government also increased awareness, encouraging Korean citizens to reduce their micropayment monthly limits.
Then, attackers tried another type of smishing.
Instead of targeting micropayments, attackers started to steal personal information from compromised smartphone through email. Trojan applications would search for information such as photos, contacts and send them to a collect server. The collect server was an email addresses hosted by a normal service provider.
According to my colleagues who were investigating early email smishing cases, there might be only one attacker or one hacking group behind the scam, because many of collect server email addresses that have been investigated had the same password.
To prevent and mitigate the damage of email smishing, we deployed countermeasures such as shutting down the collect email addresses through collaboration between the partner organizations. Shortly after, email smishing disappeared but that’s not the end of the story.
Smishing 3.0
Recently a third wave of smishing attacks has happened. Attackers are again targeting victims using SMS messages with phishing URLs for the purpose of collecting personal information. Except this time they are using using their own servers or hacking legitimate servers.
Attackers send smishing text messages which look like an invitation to a wedding or birthday party from friends or colleagues; tickets from the police; appearance orders from the prosecutor office; and package tacking information from parcel carriers.
I was almost fooled by the later, when I received a message about returning a package. I almost clicked the post, because I am an online shopping lover but luckily I questioned it!
This is a problem for many victims who click malicious URLs in online shopping related smishing messages. Because of this it is particularly prevalent during holiday periods when people are shopping online and sharing gifts. Last month the ministry of Science, ICT and Future Planning and Korea Internet & Security Agency (KISA) took steps to warn the public in the lead up to one of Korea’s biggest holidays, Chuseok.
Like the Ministry and KISA, we are working on building awareness and designing countermeasures. However, I continue to wonder what the next form of smishing will be?
Eunju Pak is Deputy Researcher General at KrCERT/CC, KISA. Prior to this she worked for KISA’s Spam Response Team.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.