
Measuring and information sharing are concepts that many cybersecurity professionals will emphasize when discussing effective information and network security.
At netlab@360.cn, we have actively tracked DDoS botnets since 2005 and make our data feeds available to the security community free of charge. One data feed that has become increasingly popular in the last year has been for the Mirai botnet.
Although Mirai is a buzzword in the security community at the moment, we’ve noticed that some of the basic concepts are not fully understood. To help clarify these, we’ve put together the following FAQ on the original Mirai.
What is Mirai?
Mirai is malware that turns computer systems running Linux into remotely controlled “bots”, that can be used as part of a botnet in large-scale network attacks including distributed denial of service (DDoS) attacks. It primarily targets Internet of Things devices such as remote cameras and smart home devices.
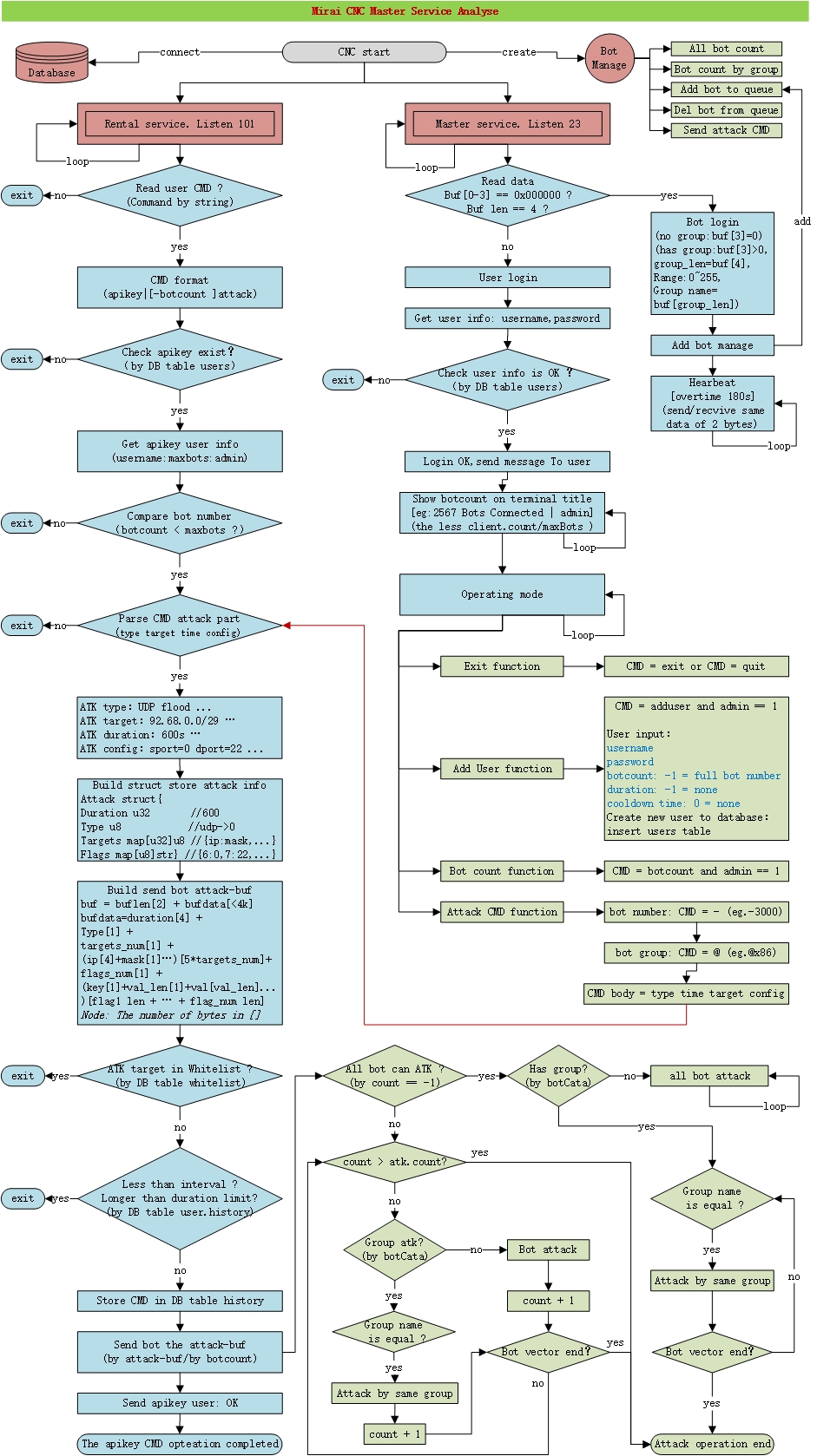
What does the Mirai C2 master service workflow look like?
Command-and-control servers (also called C&C or C2) are used by attackers to maintain communications with compromised systems within a target network. When a device is infected by Mirai botnet, the C2 will initiate two major services:
- The rental service listens on port 101 and is mainly used to provide DDoS rental service to its customers through API call
- The master service provides an interactive shell for users to log in and perform various functions
Figure 1 shows the major workflow for a C2 instance.
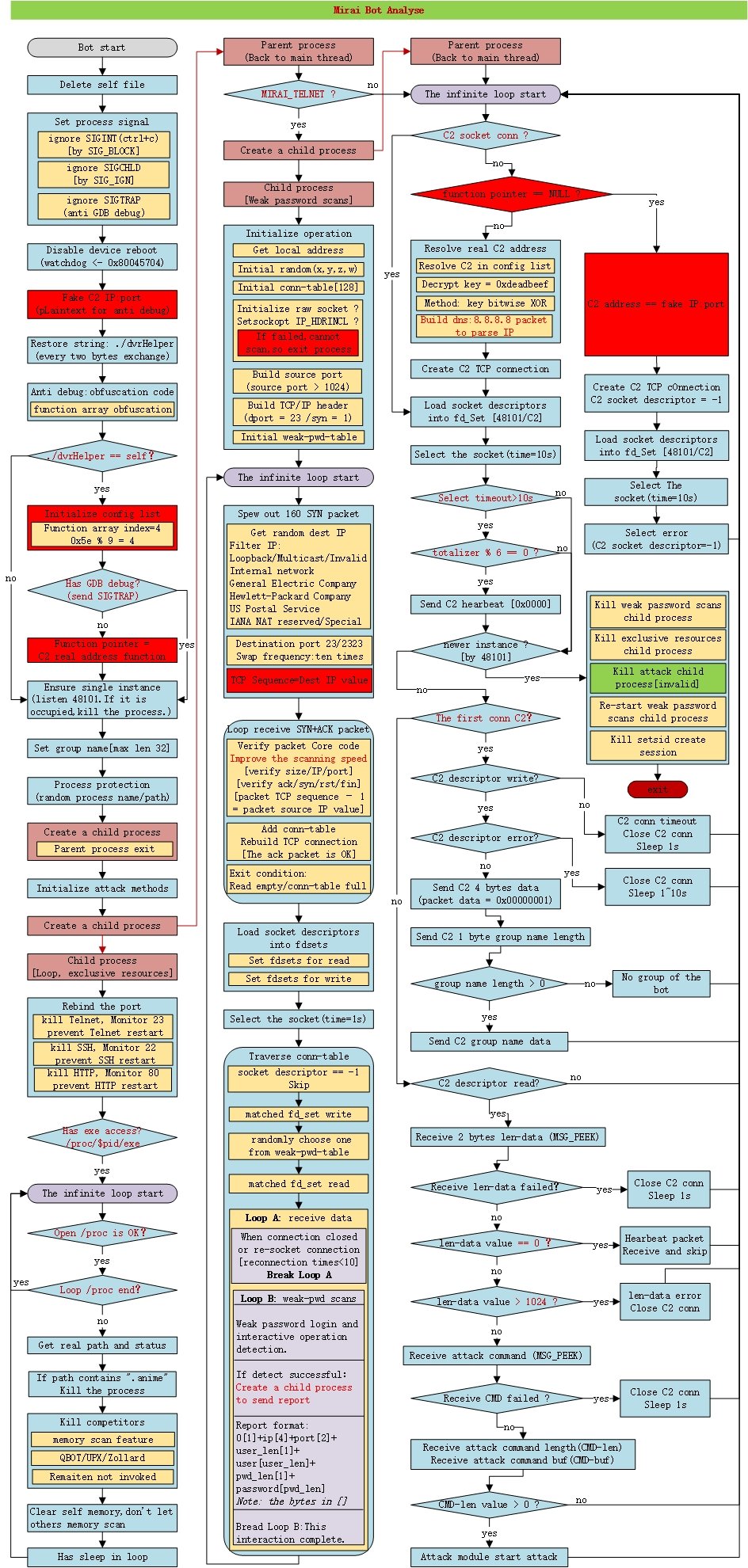
How does the Mirai bot work?
A Mirai bot has three major components: killing potential competitors on the infected host, network-wide scan for vulnerable victims and communicating with C2.
Figure 2 shows the major life cycle and the action it takes when a bot goes live on a host.
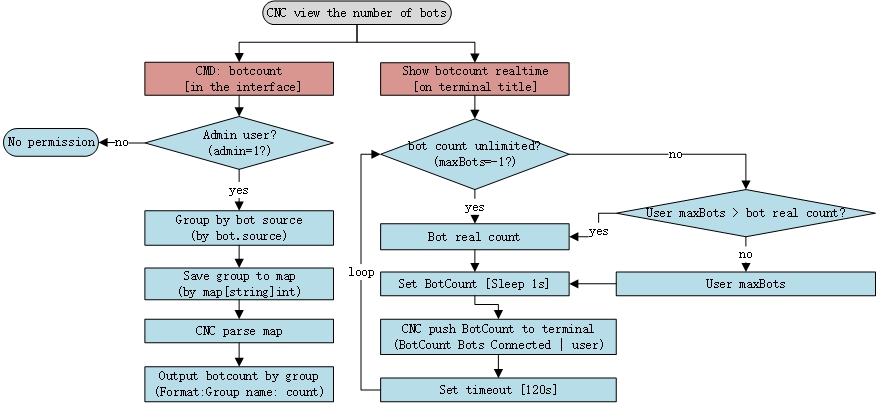
How does the C2 count the number of bots?
There are two ways to count the number of bots connected to a specific C2 (Figure 2):
- use command: botcount in the interface
- display botcount in real-time on terminal title
This applies to admin and general users.
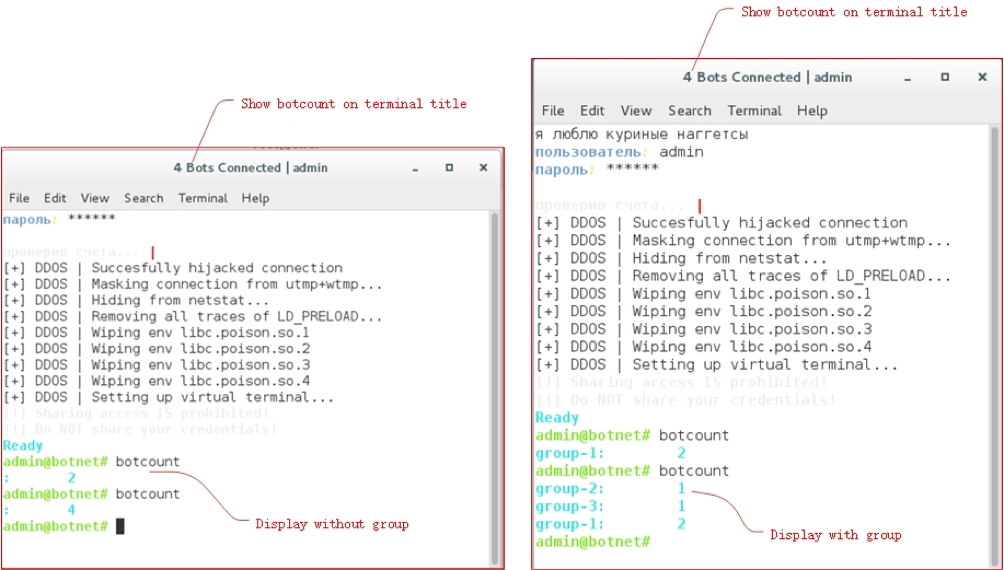
Figure 4 displays a real example of Mirai console when botcount command is executed. You can see at the current time, there are four bots connected to the C2, and then four bots belong to different botnet groups.
Does C2 have any types of users?
Yes. There are two types of C2 users:
- Admin user: The admin field in the Mirai database’s users table = 1
- General user: The admin field in the Mirai database’s users table = 0
Can users set a long duration attack, for example, 24 hours?
Admin users can set max attack duration (-1 for none) when creating a user. If the duration is -1, the attack time is in the range of 0 to 4 bytes maximum.
As an example, if user A sets a max attack duration of 30 minutes, then user A may not send attack duration longer than 30 minutes.
Can users send multiple attack commands at the same time?
No. This is because of the following two settings:
- A time interval between the two attack commands (0 for none). This is called the “cooldown time” in Mirai C2 code.
- Duration of an attack (-1 for none). This is called the “Max Attack Duration time” in Mirai C2 code.
For example:
User A sends the first attack command with a duration 25 minutes, a cooldown time of 10 minutes and max attack duration time of 30 minutes. If user A wants to send the second command, they must wait for 35 minutes (35 minutes = 10 minutes of cooldown + 25 minutes of command duration).
This applies to admin and general users.
Can history attack commands be queried?
Yes. All successful attack commands are stored in the history table of the Mirai database [a Mirai database is on the same server as C2].
Is there any way to stop the bot attack before it finishes its job?
No. Mirai does not have a command to stop an ongoing attack. Once the bot attacks, the master does not provide commands to stop it, the attack must be executed all the way to its end.
Can Mirai attack any IPs?
No. The whitelist is set by the C2 admin user, and the whitelist is stored in the whitelist table of the Mirai database. IPs in the whitelist are not allowed to be attacked unless the IPs are removed from the whitelist.
For example, if the admin user adds 127.0.0.1 to the whitelist, then the bot cannot attack itself. The same goes if the admin user adds the C2 IP to the whitelist, then the C2 cannot be attacked.
How many processes will be created after the bot launches?
At least three of the following processes will be created after the bot launches:
- A process communicates with C2 to receive attack commands
- A process clears competing malware to take all the resources
- A process scans the network for weak passwords
- If the bot receives an attack command, an attacks process will be created separately: the number of processes created = the number of attack commands (multiplied by two)
Is there any local file created after the bot is launched?
No. After the bot is executed, it will delete its own file.
Do C2 master and bot have heartbeat communication?
Yes. The heartbeat will involve sending and receiving the same 2 bytes of data (content is 0x0000). The interval time is about 60 seconds and the maximum timeout is 180 seconds.
Does the bot kill competitors?
Yes. A separate sub-process is created just for killing other botnets such as QBOT on the same devices.
How many types of DDoS attacks are there in bot?
There are ten types of DDoS attacks in bot.
- UDP flood: Straight up UDP flood
- VSE flood: Valve Source Engine query flood
- DNS flood: DNS water torture
- SYN flood: SYN flood with options
- ACK flood: ACK flood
- STOMP flood: ACK flood to bypass mitigation devices
- GRE IP flood
- Gre ETH flood: GRE Ethernet flood
- Plain UDP flood: Plain UDP flood optimized for speed
- HTTP flood: HTTP layer 7 flood
How does the bot stop the attack when there is no “stop” command provided?
The bot instance creates a child process to calculate the attack time when performing attacks. Once the attack duration is reached, the child process will kill the parent process to stop the attack.
When the attack command has multiple targets, how does it work?
The target will be attacked by the order the bots received. For example, the attack IPs are IP1, IP2, IP3, then the attack order is: IP1, IP2, IP3, IP1, IP2, IP3 and so on.
It depends. For example, Bot A receives the attack command to DDoS target IP1 for 300 seconds. Bot A immediately creates sub-process 1 for IP1 attack.
At 100 seconds, bot A receives another attack command to DDoS target IP2 for 600 seconds. Bot A immediately creates sub-process 2 for IP2 attack.
Sub-process 1 and sub-process 2 do not interfere with each other so they can run at the same time. But there is a catch: these two commands must be sent by two different users. Users must wait for one command to complete before executing the second command.
What are the characteristics in the DNS flood attack?
The default is 12-bit DNS random prefix attack; the number of prefixes can be changed by the attack command.
What are the characteristics in Plain UDP flood?
The attack source port is a fixed port. The bot binds to the port before the loop attack is executed.
What are the characteristics in GRE IP/ETH flood?
GRE ETH flood adds a custom ETH layer then GRE IP flood; the ETH layer is randomly filled. The destination IP in the packet is also randomly filled if it is not specified in the command.
Can multiple Mirai run on the same IoT device?
If more than one Mirai binds to the same port (48101), the new Mirai kills the previous process when it starts, so that only the last Mirai runs. However, if ports are different, multiple Mirai can run on the same device at the same time.
What does the bot do when a new instance is detected?
When the bot detects a new instance it terminates itself. The attack sub-process will continue to complete the attack.
What else?
netlab@360.cn has some Mirai related data and information such as a Mirai C2 tracking page and bot tracking page that is publicly available. Also be sure to check out our blog for recent news on Mirai attacks.
If you have any further questions, don’t hesitate to leave a comment or email us.
Song Bing is an information security engineer working in the Network Security Research Lab (netlab) at Qihoo 360.
The views expressed by the authors of this blog are their own and do not necessarily reflect the views of APNIC. Please note a Code of Conduct applies to this blog.

I will be grateful if you would mind helping me with these questions:
How can I simulate miria bot on an IoT device?
How can I installing mirai on vm whereas vps?
Can I have the executive source code of miria bot ?
How a new miria bot find C&C server?
How can I simulate IoT devices in VM to infected by miria bot?
Regard